Pretty much anyone who works on a computer, should know the PDF format… And many people, might use PDF encryption to protect sensitive data.
But perhaps that’s not such a great idea…
You see, PDFs use AES for encryption, which is safe, in theory… However, there are two weaknesses:
The PDF Format (Direct Exfiltration Attack)
The PDF format, only encrypts the contents of the document, not the meta-data and other information.
Now, you might think: “So? I just want the contents to be protected!”
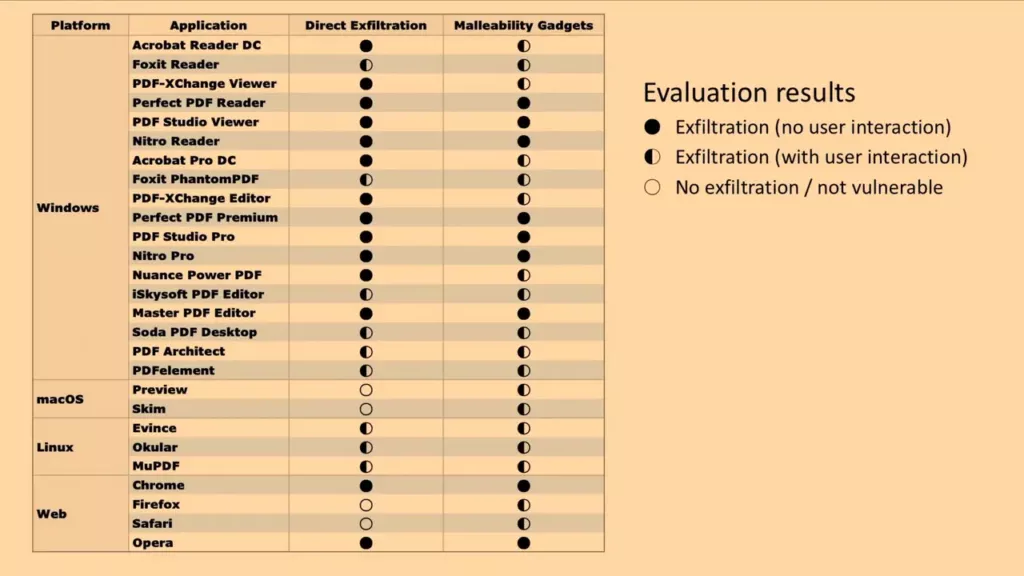
But here’s the thing: It is then possible to add some unencrypted PDF form, script or link, which simply uploads the entire contents of the PDF after decryption, to some attacker’s server. The PDF format does not protect from this tampering, and many PDF readers will gladly execute such a maliciously appended script without user interaction… This includes Adobe’s Acrobat Reader DC, which is a pretty standard reader in enterprise environments…
The good news is, the standard PDF reader “Preview” on macOS, is not affected. But many PDF readers on Windows are, and will leak the contents without user interaction.
Google Chrome, a very popular web browser, will also leak all contents without user interaction. Firefox and Safari are safe (but it can still leak if you allow submission when asked).
The PDF Encryption (Malleability Attack)
Now, let’s discuss the AES encryption… You probably heard of it as “military grade encryption”, and it’s true, it’s considered rock solid.
However, PDF uses AES in Cipher Block Chaining mode, simply known as AES-CBC. The problem with this, is that AES-CBC, unlike AES-GCM, does not perform any “authentication”, meaning it does not check whether the encrypted data has been tampered with (no integrity checks). It would be possible, to manually add authentication on top of AES-CBC, however, the PDF format doesn’t do this.
So, the attack here is, a well-known weakness of AES-CBC, where if you know part of the plain text, you can tamper with the encrypted data. And part of the plain text is known! That’s because the PDF permissions are stored both in encrypted, and plain text form. Yeah…
So, it is then possible to tamper with the encrypted data, and add some exfiltration mechanism to the PDF. Without you or the PDF reader knowing there was tampering.
Here’s a table, showing which readers are vulnerable:
What can you do about this?
- Use a PDF reader that is not fully vulnerable (see table above). Examples are Preview on Mac, Firefox and Safari, Foxit Reader.
- When asked to “submit a form” or “execute script” or “run active element” or similar, hit deny or cancel. Then contact the person who sent you the PDF and ask if that’s intended.
- Instead of using PDF encryption, use encryption outside the PDF format, like PGP (preferably with cryptographic signatures).
Keep in mind: Even if you use a PDF reader that is not fully vulnerable, all of them are vulnerable if you allow some form submission or script to run, or by clicking a link in the PDF.
If you are a techie or nerd, you can watch a full (technical) presentation on the topic here.
If you liked this article, consider donating a coffee so that I can write more. (:
I’m really glad I don’t rely on PDF encryption! Thanks for this post :)